ThinkIQ implements a role based system for managing user access to platform resources. Users are assigned to Groups, such as Registered, Engineer, Configuration, and these Groups are in turn put into Access Levels. These Access Levels – often with names mirroring the user Groups – control access to resources on the site. These access levels can be adjusted in the Admin Console of the platform. Learn more about our implementation of User Management.
To enable use of Single Sign On for your implementation of the platform, the following Groups need to be mapped to Groups in your Active Directory or AWS service. Feel free to use whatever display name you find useful when creating the group.
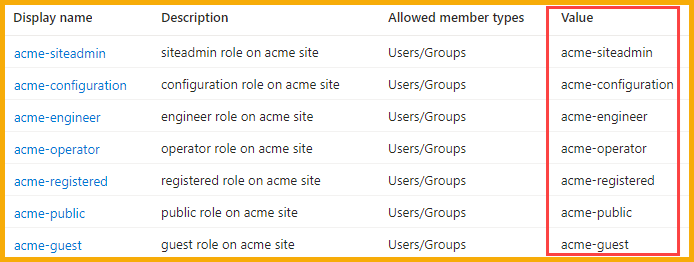
- Public – Not required in an SSO system. For other systems, this is the landing page and provides a Login button. No content is accessible by Public users.
- Registered – In general, Registered users have read-only access to the platform. They can access the Process Layout and Model Explorer, for example, but can only view content. Registered Users cannot edit site content.
- Operator – These users are configured to provide access to Manual Data Entry forms and other tasks executed by Operators.
- Engineer – Engineers have full access to technical areas of the site such as Model Explorer, Scripting, and creating custom pages with UI Components. Engineers often build the Model, map tags to attributes, create can-feed relationships, create learning content, and more.
- Configuration – This role allows access to the same resources as an Engineer and adds highly technical tasks such as Creating Connectors and doing Data Backfills.
- SiteAdmin – This role provides a convenient way for Customer Administrators to access user data and includes access to the backend of the system where User Administration occurs. SiteAdmins often are responsible for assigning new users to the appropriate Access Level. In general, SiteAdmins do not edit platform content.
For clarity, you may want to preface group names in your IdP with ‘ThinkIQ_;’ i.e., ThinkIQ_Registered.
In addition to the built-in roles, you may wish to create additional groups for access to specific parts of the Organization. For example, if you are deploying ThinkIQ across multiple sites and you wish to restrict access based on site location, we suggest you create a group in your IdP for each site. The platform will then be configured to respect these limitations. For example, if you have a site in Boise, Idaho and a site in Cedar Falls, Iowa, you could create the groups ThinkIQ_Boise and ThinkIQ_Cedar_Falls. Users in Cedar Falls would not be able to access the Boise area of the platform unless they were specifically added to the Boise group in your IdP.
Once the groups are created, contact your account manager so that the appropriate mappings on your instance can be set up and enabled.
The following is an example of the mappings in Azure Active Directory: